Nothing personal, but we don’t trust you
With the worldwide average cost of a data breach sitting at over $5 million NZ, and an average of 25,500 records impacted per incident, it’s actually hard to trust anyone these days.* If you think that’s bad, internet security giant Norton says in their Emerging Threats article that it’s only going to get worse. Gartner says that by 2020, they expect security services to account for 50% of all cybersecurity budgets.
And if you experience a breach, it’s certainly not something you can keep secret. The NZ Privacy Act 2020 will make disclosure mandatory.
A security breach is not usually anyone’s ‘fault’ (apart from hackers and the rare disgruntled employee). But your business also has a responsibility of care to protect your network and to keep up with best and current practice. By not owning up to that responsibility, you – yes YOU – can easily and unknowingly be the person who leaves the gate open to your valuable data, and the ‘Help Yourself’ sign on the door.
Why the traditional approach to securing your network is no longer enough
While it used to do the job, these days, securing only the perimeter leaves the inner network painfully vulnerable.
Why? The threat landscape has changed. All it takes is one employee to plug in a USB drive, click on a phishing email, or reuse a password, and your expensive perimeter firewall is rendered irrelevant – and there’s nothing to stop the attacker moving further through the network. The wide-open spaces of an internal network with no authorisation controls in place provide fertile ground for data theft, ransomware, or worse. Business stakeholders are left holding this risk with no way to influence or manage it – not a comfortable position.
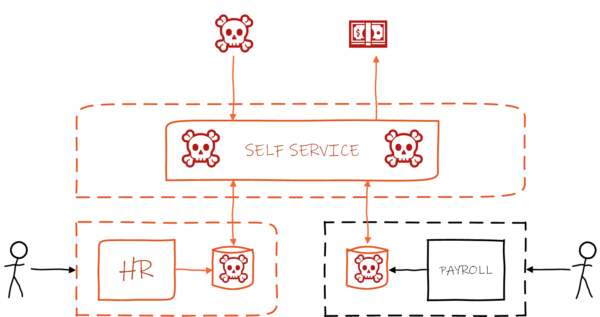
Once a single system is breached, an attacker can leverage a lack of controls to move through the network.
The reality is that organisations generally fail to comply with modern security standards. Even if you are deploying the latest SaaS-based widget making platforms, the chances are that there are at least a couple of 20-year-old systems running under a desk that everyone’s too scared to touch – and you are only as secure as your weakest link.
While it may sound brutal, we say trust no one. And here’s how to do it.
As your business stands to lose both reputation and money, the Zero Trust Network security model is the only safe approach to protecting your network.
Zero trust is based on the principle of maintaining strict controls as to who can access the network. Without exception. This includes those who are already inside your network perimeter. In fact, zero trust treats accessing the internal network in the same way as accessing the external network by rigorously applying both authentication (who are you?) and authorisation (are you allowed to access this?) at all points.
While it may sound draconian, a Zero Trust Network offers substantial business benefits.
First, it reduces the risks of data breach within your organisation. It also increases business speed and agility as your network isn’t in constant shutdown mode while breaches are countered. You gain more control over your environment, on-premise and cloud alike, and can focus on the application workload, rather than the security perimeter endpoint. And a ‘no trust’ relationship mean no potential impacts to connected systems when one system changes.
A Zero Trust Network makes risk and security compliance audits easier by enabling modern authorisation methods to your backend systems.
Zero trust networks with legacy systems
Zero Trust Networks rely on using modern authentication and authorisation standards to provide interoperability between all platforms, so how do you achieve this in the real world when you have a mixture of new and legacy systems?
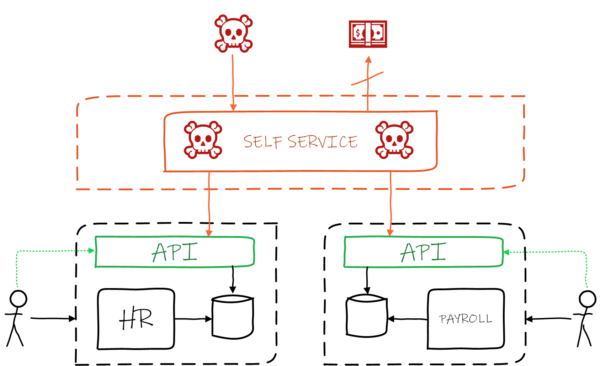
Instituting modern authentication and authorisation can stop attacker movement, protecting systems.
Our recommended approach to allowing your legacy systems to operate in a zero-trust environment is to leverage API Gateways as a façade. These API Gateways enable us to manage access to legacy systems using industry-standard methods such as OAuth without having to modify the backend systems. We can subsequently allow your network to present data to different audiences, based on Authorisation and Claims, e.g. exposing an API for vendor/external client to access.
Using API Gateways allows business owners to take control of the access to their own platforms. By designing and defining security permissions upfront, it helps to prevent and protect you from both external malicious attacks such as DDoS (distributed denial-of-service) and internal attacks such as a disgruntled employee.
Adaptiv use leading solutions like Microsoft Azure API Management, MuleSoft API Gateway or Boomi API Management to deliver API Management solutions for clients. As having multiple API Gateways can introduce complexity in managing the network, we also leverage modern CI/CD toolkits such as Azure DevOps to ensure a consistent and coherent delivery across the enterprise.
Suzanne Collins, author of The Hunger Games, wrote: “For there to be betrayal, there would have to have been trust first.” With a Zero Trust Network, no-one can let you down, deliberately or otherwise.
Author: Philip Durrant – Principal Consultant
Co-Author: Harris Kristanto – Consultant
The opinions expressed in our blogs are those of the individual contributors, not necessarily those of Adaptiv Integration. We encourage our people to lead, not follow, and to add value by sharing their experience and unique insights.