There are several ways to raise business notifications in Azure Logic Apps. One way is to add an Office365 or SendGrid email action directly to the Logic App. Another is to call a common Logic App that handles sending emails to appropriate audiences. Perhaps another option is to send notification details to a Service Bus Queue or Topic that is subscribed by the common Logic App.
Each of these approaches have certain limitations:
- If using an email action directly in a Logic App then each Logic App must know the destination email address.
- An email action also makes it difficult to change how notifications are sent e.g., switch from Office365 to SendGrid, or add another destination like PagerDuty.
- Sending notification requests from your Logic Apps also means the decision to send a notification is baked into the Logic App. Changes to notification rules may mean changing many Logic Apps.
Leverage Log Analytics and Alert Rules
A better approach is to abstract away completely the sending of notifications from the source. Data that could potentially be used for a notification are written to Log Analytics. Alert Rules are created over these data that will trigger when a business notification should be sent. The Common Alert Schema supplied by the Alert Rule is used by a generic Logic App that sends business alerts.
This method solves the issues of the other approaches.
- The source Logic App does not need to know about how a business notification is sent or to whom.
- The source Logic App doesn’t even need to know that a notification needs be raised.
- The notification handler can be changed independently.
- Alert Rules contain the logic for raising notifications and can be changed independently from the source.
- The data written to Log Analytics may be used for more than just notifications.
This article describes how to use Azure Log Analytics to generate business notification emails from Logic Apps.
Log Analytics for Logic Apps the Easy Way
Log Analytics is ideal for raising business notifications. A simple method is to use a Log Analytics Custom Log monitored by an Alert that runs a Logic App responsible for formatting and sending an email to a business user. This method minimises the amount of data that are sent to Log Analytics.
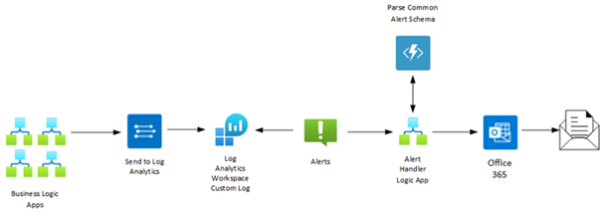
How It Works
Any Logic App that needs to email a business user writes details to a Custom Log using the Azure Log Analytics Data Collector Send Data action:
This action sends name-value pairs to a custom log of your choice. If the custom log name does not exist, then it will be created automatically.
An Alert Rule that regularly queries the custom log is triggered and calls an Alert Handler Logic App passing an Azure Monitor Common Alert Schema message. This message contains a generic data set containing the details written from the original Logic App.
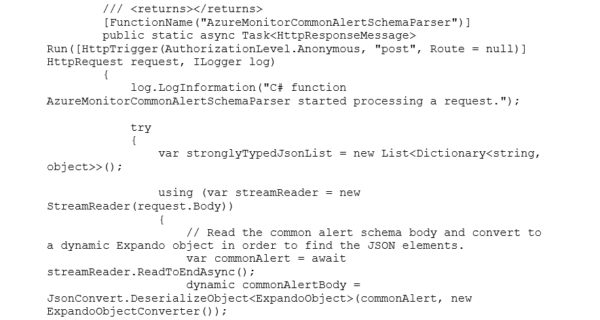
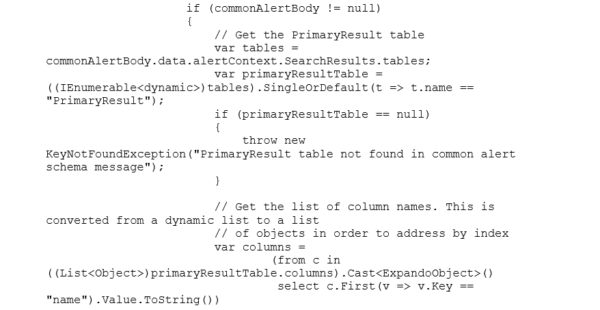
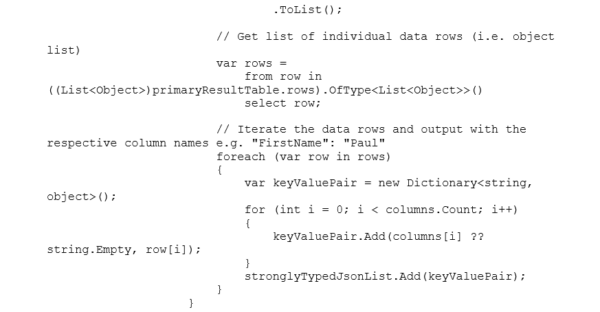
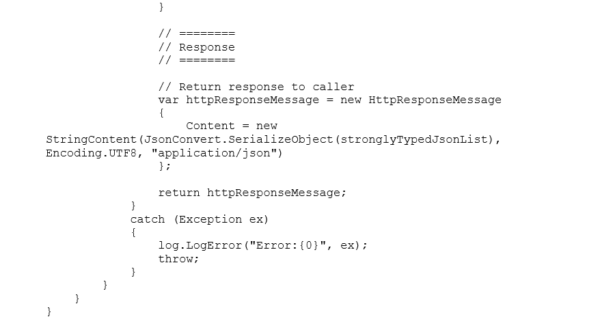
The Alert Handler Logic App uses an Azure Function to parse the generic data set into a “strongly typed” JSON message that can be parsed, and the values used to create an HTML formatted email.
Steps To Set Up
The following artifacts need to be set up to support business notifications:
- Log Analytics Workspace
- Azure Monitor Common Alert Schema message parse Function
- Alert Handler Logic App
- Azure Alert to monitor for new log messages
- Send Data action in business Logic App
You must create at least one workspace to use Azure Monitor Logs.
- Search for Log Analytics workspaces in Azure Portal
- Click +New and enter subscription, resource group, workspace name, and region
- Select a pricing tier (learn more…). Pay-As-You-Go is sufficient for low volume logs, e.g., business exceptions
- Enter Tags if needed, Review, then create. Workspace creation may be templated
“The common alert schema standardizes the consumption experience for alert notifications in Azure. Historically, the three alert types in Azure today (metric, log, and activity log) have had their own email templates, webhook schemas, etc. With the common alert schema, you can now receive alert notifications with a consistent schema.” (Microsoft Docs link)
The area of interest in the common alert message is alertContext SearchResults. The SearchResults section contains a table of alert details that is split into a list of column names and then an array of related rows, each of which is an array of string
Common Alert Message alertContext SearchResults

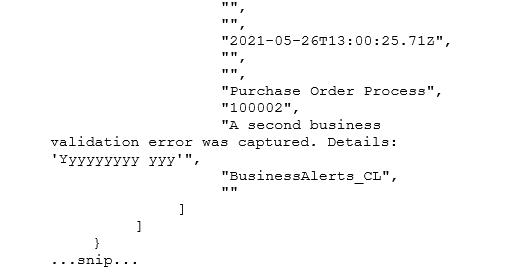
You can see the arrays are not conducive to parsing in a Logic App Parse JSON Data Operation. An Azure Function is used to create a “strongly typed” array:
“Strongly Typed” JSON

Create a function with the following code to parse the common schema message and produce the “strongly typed” JSON message.
Azure Monitor Common Alert Schema Parser Function
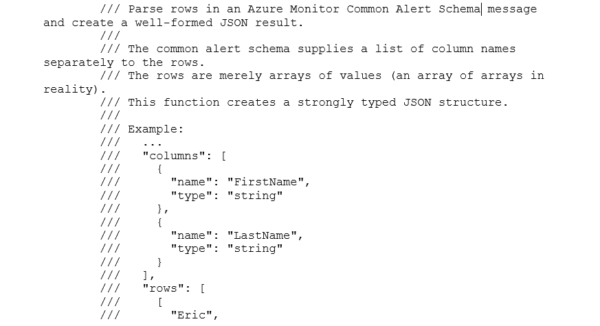
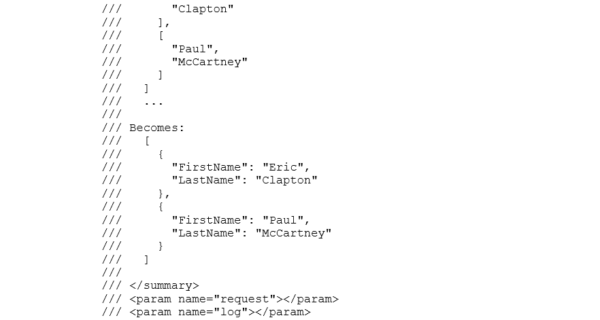
Alert Handler Logic App
The Alert Handler Logic App receives Azure Monitor Common Alert Schema messages from an Azure Alert. This Logic App can do pretty much anything you want with an alert but in this example an HTML formatted email is sent to a selected business user email address.
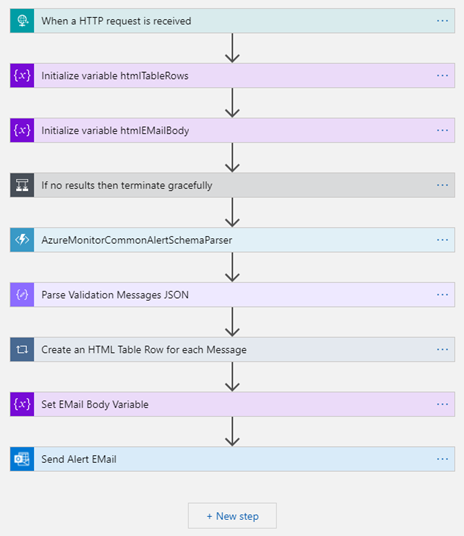
If no results then terminate gracefully

If ResultCount is zero, then no alerts are contained in the message – terminate with Succeeded
@triggerBody()?[‘data’]?[‘alertContext’]?[‘ResultCount’] is greater than 0
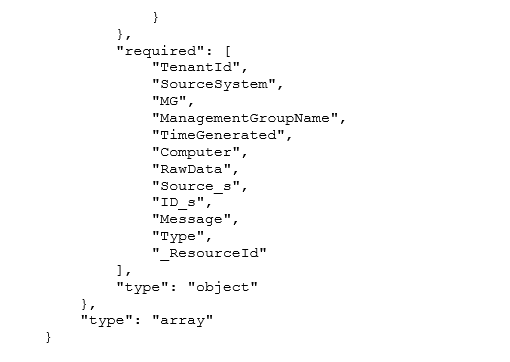
Parse Validation Messages JSON

Create a schema that matches the “strongly typed” alert message that is emitted by the parser function.
“Strongly Typed” Schema Example

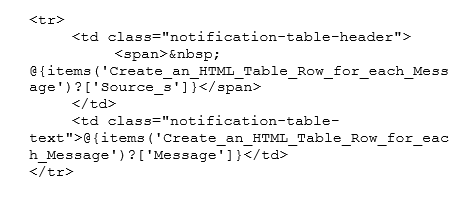
Create an HTML Table Row for each Message
Multiple alert rows can be formatted into a table for presentation in the email body.
Set EMail Body Variable

Compose the HTML email body with the table rows created above. The HTML email body should use styles for a professional appearance.
Send Alert Email

Set the email body to the HTML variable, set a subject, and send to a configured email address.
Azure Alert to monitor for new log messages
Search for Alerts in the Azure Portal.

Click + New alert rule

Select the Log Analytics workspace created earlier as the Scope resource.

Create a Condition with an optional where clause

Set Alert logic to be Number of results Greater than 0 threshold value.

Evaluate the alert on a Period of 5 minutes with a Frequency of 5 minutes
Add an Action with an Action Type of Logic App and select the Alert Handler Logic App created earlier.
Set Alert rule details e.g., Severity
Send Data action in Business Logic App
All that is required in the Business Logic App is to send a simple JSON body to Log Analytics using the Send Data action.